Dec 8, 2023

Ransomware seems to be everywhere these days. You’ve probably heard countless stories in the news about businesses forking over large sums of cash to get access back to their critical sensitive information, or worse, about the fallout from companies that refused to pay the ransom.
Ransomware is one of the scariest of all the malicious programs out there. Stories often portray it as happening suddenly with no time to react. Innocent businesses are asked to pay ludicrous amounts of cash in cryptocurrency payments or risk having their entire digital business infrastructure nuked and their best-protected trade secrets sold online to the highest bidder.
But the truth is, there is a method to ransomware attacks that all hackers follow. Knowing the stages of a ransomware attack is critical to understanding how to detect and thwart them before they become a huge problem.
In today’s guide, the St. Louis cybersecurity experts at Blade are here to shed light on this nefarious threat and, hopefully, give you the confidence to protect yourselves against it.
What is Ransomware?
We should probably start from the beginning. Ransomware is a cyberattack in which threat actors access sensitive information by compromising your network. They then encrypt your files so you can’t access them and demand a ransom payment for the decryption key, hence the ransomware.
It is a particularly nasty form of malware attack that can cripple businesses and destroy the devices and networks you depend on daily to keep everything running.
A particularly salient example is the breach of MGM Resorts and Caesars Entertainment, the companies behind the giant Las Vegas and Atlantic City casinos. The attack caused business to halt, causing millions of dollars in losses daily for the casinos. While MGM stood its ground and refused to pay the hackers, Caesars caved and negotiated a $15 million payment for releasing their critical systems and promised that stolen customer data would not be leaked or sold.
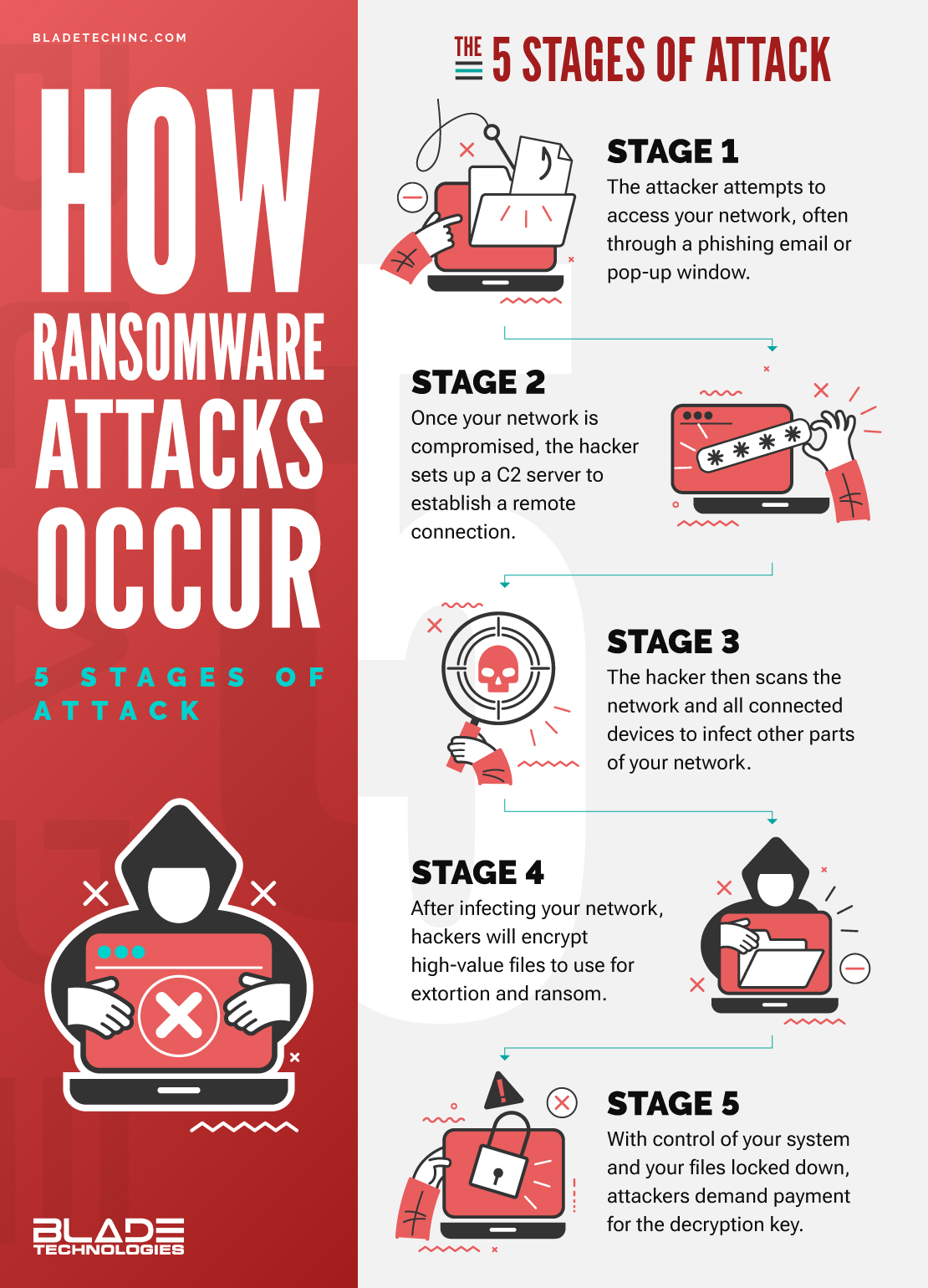
What Are the Stages of a Ransomware Attack?
Ransomware attacks typically unfold in five stages, from the threat actors gaining access to critical systems to the initial ransom demand.
1. Initial Infiltration
All ransomware attacks start with the attacker attempting to access an organization’s network. Cybercriminals use many attack vectors, but phishing emails are the most common tactic. A phishing email is a social engineering tactic where threat actors pose as legitimate persons or organizations and attempt to get an employee to click on a link or download a ransomware payload file.
2. Command and Control Setup
Once a hacker has successfully compromised your network, they quickly begin making themselves at home, establishing a foothold. They set up a command and control (C2) server. This occurs when the ransomware program officially establishes a connection to the hacker’s device and is used to send further attack signals to your network from their remote location.
They can also use the command and control server to infect your system with further strands of ransomware for a multi-pronged attack.
3. Network Scanning and Lateral Movement
Once the ransomware group establishes a beachhead or the initial breach point in the system, the next step involves assessing the environment. This involves scanning the network, cloud storage, and all connected devices to understand the layout, security measures, and potential data targets.
Once they complete their scan, they begin lateral movement, infecting other parts of your network with ransomware to gain more access. During this phase, they may target and infect privileged accounts to authorize themselves to enter more secure areas of your network or to pass through network segmentations.
4. File Encryption
During this stage, the hackers locate high-value files and begin encrypting them. Some more sophisticated ransomware strains use data exfiltration to copy critical files before deleting backups and encrypting the originals.
They may use this in a double extortion ransomware attack where they demand payment to unencrypt your files and another fee to prevent the release or sale of sensitive information.
The result is that your employees are locked out of your system and unable to continue normal business operations until you receive a decryption key.
5. The Ransom Demand
Once hackers are confident that they have sufficiently seized control of your system and locked down your most important files, they’ll reach out with a demand for payment.
In most cases, they will ask that you pay them a large amount of money in untraceable cryptocurrencies to receive the decryption key for your files. They will usually set a few days’ deadline and raise the ransom amount if you fail to meet it.
How to Minimize Damage from Ransomware Attacks
There are several steps your business can take right now to minimize any potential fallout from a ransomware attack. Regarding ransomware, preparation and good digital hygiene are often the best defense against data breaches.
Here are just a few tips from the cybersecurity experts at Blade Technologies for your digital security teams.
Have an Incident Response Plan
An incident response plan is one of the most crucial things you need to have in place before a ransomware attack hits your company. This important document should be formulated with the combined power of senior staff, your IT department, and possibly legal counsel if you deal in sensitive customer data that may lead to lawsuits if leaked.
Your incident response plan should lay out precisely what to do in the case of a data breach. It will list steps on how to respond to an incursion, how to minimize damage after the attack, and what everyone’s role is in the process.
Have Data Backups. Lots of Them
If cyber criminals can’t get all of your data, they can’t successfully hold it hostage. The best way to avoid being caught with all your data gone and hackers holding all the keys is to back up your data frequently. Having data backups allows you to restore your systems with minimum disruption.
Even if this doesn’t stop ransomware from wrecking your systems (cyber thieves may choose to delete your data when they realize they can’t ransom it), it helps you get back on your feet faster after an attack.
However, while having data backups is good, you may consider hosting them outside your main network and away from cloud servers. As we discussed, some more sophisticated ransomware programs will actively seek data backups and exfiltrate files, then delete them to ensure you’re forced to pay the ransom.
Keep Operating Systems and Software Updated
One of the best things you can do to make yourself less of an appealing target to hackers is to ensure that all your software is updated to the latest version. Software vendors will frequently publish security patches that remove vulnerabilities threat actors may try to exploit to get a foothold in your system.
Keeping software up-to-date ensures that all currently known program vulnerabilities are accounted for. However, this isn’t foolproof. As we’ve discussed in our zero-day and supply chain cybersecurity guides, sometimes hackers find a security loophole before software vendors can patch it. Check out our guides to learn more about how to protect yourself in those scenarios.
Keep Your Staff Informed
As we’ve discussed in our guide on How to Prepare for Ransomware Attacks, training your employees to recognize and thwart cybersecurity threats is critical to avoid becoming a victim.
Most ransomware attacks begin when an employee unknowingly clicks on an infected link from a phishing email or pharming website. Keeping employees aware of current cyber scamming tactics can help you stop a ransomware attack before it begins.
Partner with Blade Technologies
Blade Technologies is one of the best cybersecurity management firms in the St. Louis region. Our threat assessment, data security, and data breach remediation services have helped companies avoid inevitable catastrophes from unscrupulous cyber thieves.
Contact the experts at Blade today, and let’s protect your data together.
Contact Us